What is Penetration Testing?
A penetration test or pen-test refers to the ethical hacking service, a pre-approved simulation of a real cyber-attack on a network or web application or system, that evaluates both weaknesses as well as strengths of a system when confronted with a cyber-attack. The benefits of this authorized cyber treat simulations are vast, as your in-house team may not always be aware of the constantly evolving cyber-vulnerabilities, digital and web risks.
For example, in the context of specifically a web application or system security, pen-testing is used to continually augment a web application or system firewall for example. Pen-testing services may include the tentative breaching of any of your application systems like application protocol interfaces (APIs), frontend/backend computer systems, to find weaknesses, like unsecured inputs and vulnerabilities.
A penetration test target is a white package (which gives back ground and system information) or black box (which supplies only standard or no information except the company title). A gray industry penetration test is an assortment of both (where limited understanding of the mark is shared with the auditor). A penetration test can validate whether a cyber-penetration method is susceptible to hit when defenses was indeed adequate, and which defenses (if any) the pen-test defeated.
Security breaches that the penetration test uncovers are reported towards the system owner or administrator. To reduce your cyber security risks, the penetration test reports may also examine the security effects of the cyber-attack toward your company and advise optimum countermeasures (services, systems or solutions) to scale back the exposed threat.
The Pen Testing Assessment Process Stages
- Planning, gathering data, defining the objectives of a test, like the framework and methods to be used for the pentest.
- Scanning for vulnerabilities using various penetration attempts via static and dynamic analysis.
- To uncover the vulnerabilities of your web application the pen-testing team will try to gain unauthorized access to your system, to prove the system risk. Some examples of gaining access are gaining system privileges, SQL injections, stealing data, diverting website traffic.
- In this stage, the testing team will try to maintain the vulnerability state of the system, to get in-depth access imitating advanced persistent threat to your network or systems. There are countless examples of long-term company exposure to threats, seamless to the overall security team but presenting a insurmountable risk value once they were discovered.
- Reporting the actual positive results of the vulnerabilities and cyber-risk assessment outlines the uncovered threat, the exposed sensitive data and information from your network, mobile or digital assets and how long such a situation can persist with your system as an undetected threat.
You company security officer or team evaluate the report findings and patch your system to protect it against real web cyber-attacks, application security risk or network threat.
Standard penetration testing frameworks
Pen-testing are a critical component of your cyber security systems assesments. Standard frameworks for conducting penetration and vulnerability testing are
- the Open Source Security Testing Methodology Manual (OSSTMM),
- the Information System Security Assessment Framework (ISSAF)
- the OWASP Testing Guide.
- the Penetration Testing Execution Standard (PTES),
- the NIST Special Publication 800-115.
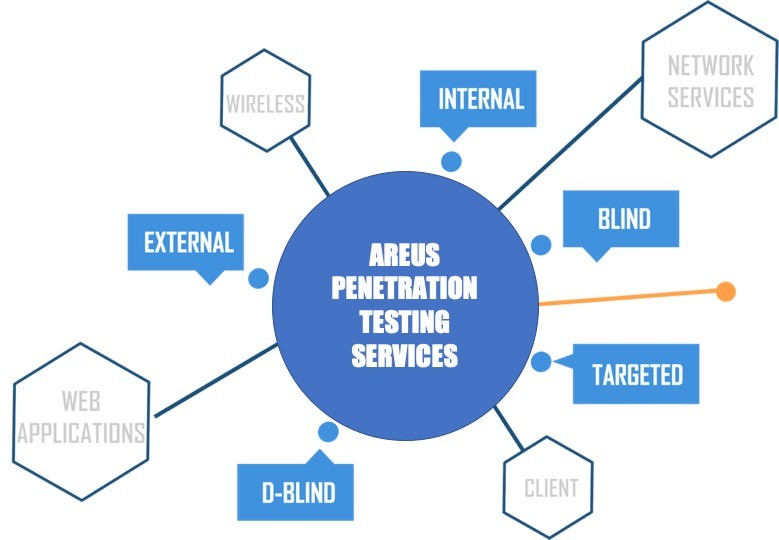
Pen-testing scenarios and penetration testing services
External Testing
External testing , targets the assets of a business which are already available on the web, like a web or mobile application, the exposed network, the e-mail and URL of your website devices (domain name servers - DNS). This type of penetration testing targets phase 3 and 4 of the vulnerabilities testing process described above, so that the testing team gets access and plants information into your vulnerable systems.
Internal Testing
A second attempt to expose your cyber-risk can be made internally. In an inside test, a tester that was granted the access to an application behind the firewall simulates an attack by a malicious insider, like a rogue employee, or accidentally exposing or gaining access to someone's credential to the system. The white box pen-testing services imply that the tester would be provided with some security info ahead of time.
Blind Testing
The biggest vulnerabilities may be found through a blind test aka black box pen test , a pen-tester is provided with just the company name. This gives your security team the real feel of the cyber attack and the real threat that your company is exposed to.
Double Blind Penetration Testing
A variation of the cyber-attack may the double blind penetration testing services ( aka covert penetration testing solutions) , when your team is not aware of the simulated threat giving everyone a real feel of the risk, without prior notice of the potential breech.
Targeted Testing
One of the recommended scenarios if you are aware already of some of your cyber risk is for tour team and the testing company work together on a common scenario; this allows for a great training of your team into what and how a hacker actually acts and ho the threat is being unfolded through your network, allowing for your team to react immediately to the risk.
VULNERABILITY ASSESSMENT & PENETRATION TESTING
Bespoke Cyber Security Service and Solutions Packages
ONBOARDING PACKAGE
IDEAL FAST CYBER VULNERABILITIES ASSESSMENTS
✓ 20 h Manual Pen-testing
✓ Automated Web App Testing and access to proprietary platform and live vulnerabilities dashboard
✓ Risk Evaluation Score
✓ Final report on exposed vulnerabilities
✓ Recommendations for fixing your vulnerable systems
IDEAL REGULAR HEALTH CHECK-UP OF YOUR INTERNET ASSETS
REGULAR HEALTH ASSESSMENT
✓ 50 h Manual Pen-testing
✓ Automated Web App Testing and access to proprietary platform and live vulnerabilities dashboard
✓ Risk Evaluation Score
✓ Final report on exposed vulnerabilities
✓ Recommendations for fixing your vulnerable systems
✓ Live support on request
ENTEPRISE VULNERABILITIES CHECK
IDEAL METICULOUS EXAMINATION OF A LARGE SYSTEM
✓ 80 h Deep dive and penetration testing
✓ Network, infrastructure and architecture security analysis, including code
✓ Automated Web App Testing and access to proprietary platform and live vulnerabilities dashboard
✓ Risk Evaluation Score
✓ Final report on exposed vulnerabilities
✓ Recommendations for fixing your vulnerable systems
✓ Live support in implementing and patching the systems
Our case studies
BENEFITS OF WORKING WITH US
Minimized costs
Lower operational and labor cost by more than 50%
Express services
Get tasks completed overnight and be certain that everything is up and running in the morning
Expert teams
Our people have the extensive knowledge and raw energy for any kind of projects
Flexibility
Create your custom team and have total control of the workflow and planning
Less workflow
You can focus on more important tasks
START YOUR PROJECT WITH AREUS TODAY!
We’d love to hear from you! Write us and find out what we can do for you.











